An overview about VPN
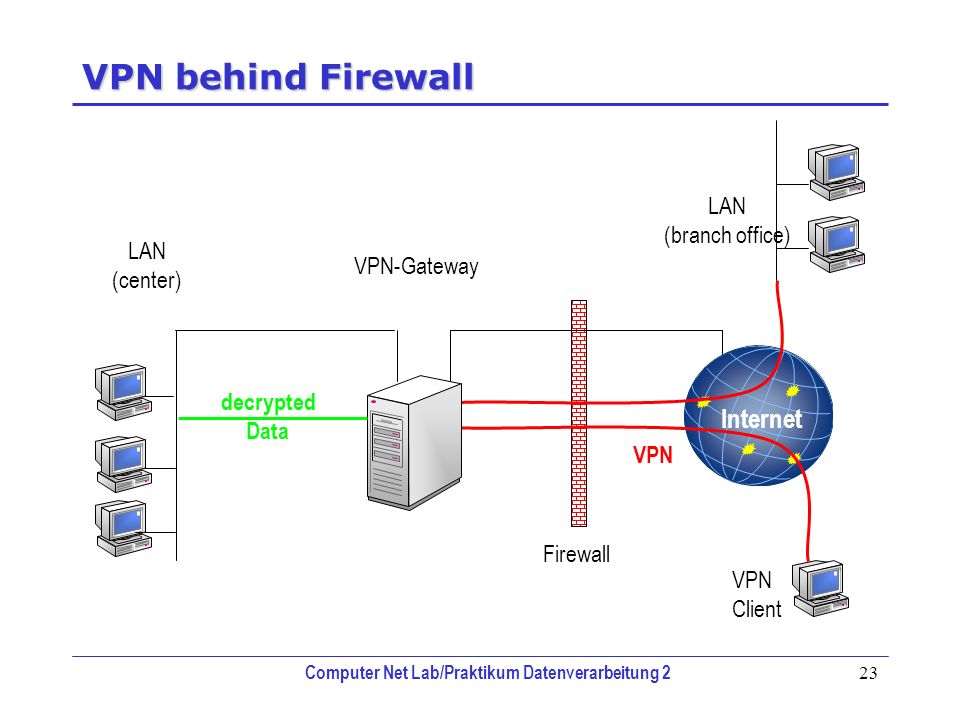
Virtual Private Network is a technology that allows one to remotely connect to a private network, so that they are virtually connected to that network, as though they are on-site and plugged into the LAN. The aim of a Virtual Private Network is that it provides users with the ability to access a private network from a remote unsecured point outside of that network. VPN helps the remote workers to connect to office resources without needing to be physically in the office. There are many different VPN protocols and types of VPN’s and the LAN-to-LAN VPNs are used to connect multiple networks.
The secured network:
A VPN creates a tunnel through unsecured networks that can be used by the clients to access their private network without interference from the rest of the unsecured networks. Therefore VPNs have to transmit private information across unsecured networks and should make sure that data exchanged across these networks is kept secure by employing a combination of encryption on the data packets and authentication to allow access to only those users with permission. A secure VPN uses cryptographic tunneling protocols and this protocol keeps confidential information and it should prevent unauthorized access and protects private data. One should be aware of the proper selection, implementation, and usage of a VPN system to have a secured communication over an unsecured network. There are many insecure VPN products on the market and hence the users should thoroughly investigate the products before purchasing any vpn technology.
Advantages:
In countries like China, there are certain restrictions on their freedom to access all content on the internet. The tool has also grown in popularity with users in these locations, where VPNs can be used to establish a private connection to private networks in unrestricted locations. Now they can effectively browse the internet as if they were in that unrestricted location. For many VPN clients, the preferred solution may be to open an account with a VPN provider (such as hola vpn, uVPN, ZenMate and etc) rather acquiring-the-shelf VPN software so that they benefit from the extra services including technical support, advanced security protection, malware protection, and monitoring software.
